搜索结果: 1-15 共查到“DETERMINISTIC”相关记录144条 . 查询时间(0.063 秒)
The Local Forking Lemma and its Application to Deterministic Encryption
Deterministic public-key encryption searchable encryption forking lemma
2019/9/16
We bypass impossibility results for the deterministic encryption of public-key-dependent messages, showing that, in this setting, the classical Encrypt-with-Hash scheme provides message-recovery secur...
Arcula: A Secure Hierarchical Deterministic Wallet for Multi-asset Blockchains
Hierarchical Deterministic Wallet Hierarchical Key Assignment Bitcoin Blockchain
2019/6/19
This work presents Arcula, a new design for hierarchical deterministic wallets that significantly improves the state of the art. Arcula is built on top of provably secure cryptographic primitives. It ...
In cryptocurrencies such as Bitcoin or Ethereum users control funds via secret keys. To transfer funds from one user to another, the owner of the money signs a new transaction that transfers the funds...
Attribute Based Encryption for Deterministic Finite Automata from DLIN
Attribute-based encryption deterministic finite automata decisional linear assumption
2019/6/5
Waters [Crypto, 2012] provided the first attribute based encryption scheme ABE for Deterministic Finite Automata (DFA) from a parametrized or ``q-type'' assumption over bilinear maps. Obtaining a cons...
On ELFs, Deterministic Encryption, and Correlated-Input Security
deterministic public key encryption lossy functions
2019/2/28
We construct deterministic public key encryption secure for any constant number of arbitrarily correlated computationally unpredictable messages. Prior works required either random oracles or non-stan...
Deterministic Identity-Based Encryption from Lattice-Based Programmable Hash Functions with High Min-Entropy
deterministic identity-based encryption adaptively secure auxiliary-input
2019/1/26
There only exists one deterministic identity-based encryption (DIBE) scheme which is adaptively secure in the auxiliary-input setting, under the learning with errors (LWE) assumption. However, the mas...
Most classical consensus protocols rely on a leader to coordinate nodes’ voting efforts. One novel idea that stems from blockchain-style consensus is to rely, instead, on a “longest-chain” idea for su...
Deterministic Cube Attacks: A New Method to Recover Superpolies in Practice
Trivium cube attacks key recovery attack
2018/11/12
Cube attacks are an important type of key recovery attacks against NFSR-based cryptosystems. The key step in cube attacks closely related to key recovery is recovering superpolies. However, in the pre...
Differential Fault Attacks on Deterministic Lattice Signatures
differential fault attacks post-quantum cryptography lattice-based cryptography
2018/4/19
In this paper, we extend the applicability of differential fault attacks to lattice-based cryptography. We show how two deterministic lattice-based signature schemes, Dilithium and qTESLA, are vulnera...
Non-Interactive Delegation for Low-Space Non-Deterministic Computation
delegation non-interactive succinct arguments
2018/1/2
Our scheme consists of only two messages and has adaptive soundness, assuming the existence of a sub-exponentially secure private information retrieval (PIR) scheme, which can be instantiated under st...
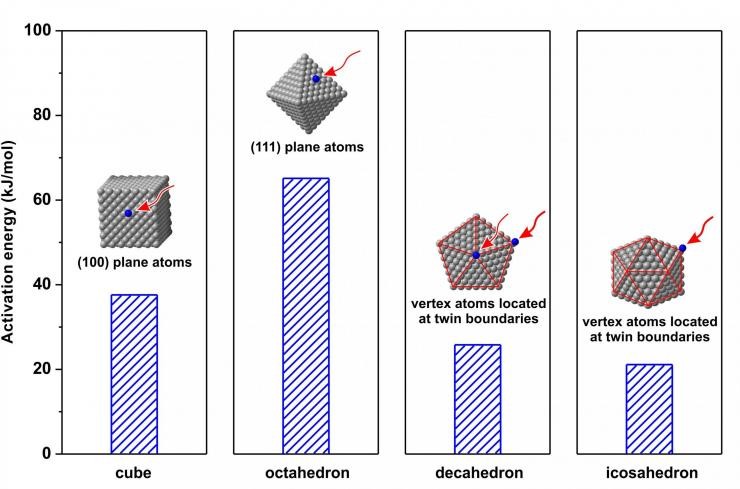
Project Will Provide Reaction Kinetics Data For Deterministic Synthesis Of Metallic Nanocrystals(图)
Reaction Kinetics Data Deterministic Synthesis Metallic Nanocrystals
2018/1/10
Researchers have published the first part of what they expect to be a database showing the kinetics involved in producing colloidal metal nanocrystals – which are suitable for catalytic, biomedical, p...
Attacking Deterministic Signature Schemes using Fault Attacks
Deterministic signatures EdDSA fault attack
2017/10/19
Many digital signature schemes rely on random numbers that are unique and non-predictable per signature. Failures of random number generators may have catastrophic effects such as compromising private...
Differential Fault Attacks on Deterministic Signatures
Public-key algorithms Elliptic curve cryptography Digital signatures
2017/10/9
Deterministic signature schemes are becoming more popular, as illustrated by the deterministic variant of ECDSA and the popular EdDSA scheme, since eliminating the need for high-quality randomness mig...
Write-Only Oblivious RAM (WoORAM) protocols provide privacy by encrypting the contents of data and also hiding the pattern of write operations over that data. WoORAMs provide better privacy than plain...
Evidence for the Deterministic or the Indeterministic Description?--A Critique of the Literature about Classical Dynamical Systems
determinism indeterminism randomness underdetermination ergodic theory stochatic processes dynamical systems
2016/5/31
It can be shown that certain kinds of classical deterministic descriptions and indeterministic descriptions are observationally equivalent. In these cases there is a choice between deterministic and i...

