搜索结果: 1-15 共查到“share”相关记录89条 . 查询时间(0.078 秒)

Small stars share similar dynamics to our sun, key to planet habitability
magnetic activity cool stars magnetic environment
2021/8/10
Scientists show that 'cool' stars like the sun share dynamic surface behaviors that influence their energetic and magnetic environments. Stellar magnetic activity is key to whether a given star can ho...

Modern humans, Neanderthals share a tangled genetic history, study affirms(图)
Modern humans Neanderthals tangled genetic history
2020/4/17
In recent years, scientists have uncovered evidence that Neanderthals and modern humans interbred. Previous research has shown that Neanderthals who were connected to the Vindija Cave in modern-day Cr...
Our conjecture emerges after introducing the notion of convec set for an access structure, a subset of nn-dimensional real space. We prove several topological properties about convec sets and raise se...
How to (not) share a password: Privacy preserving protocols for finding heavy hitters with adversarial behavior
passwords secure computation differential privacy, heavy hitters
2018/1/12
Bad choices of passwords were and are a pervasive problem. Most password alternatives (such as two-factor authentication) may increase cost and arguably hurt the usability of the system. This is of sp...
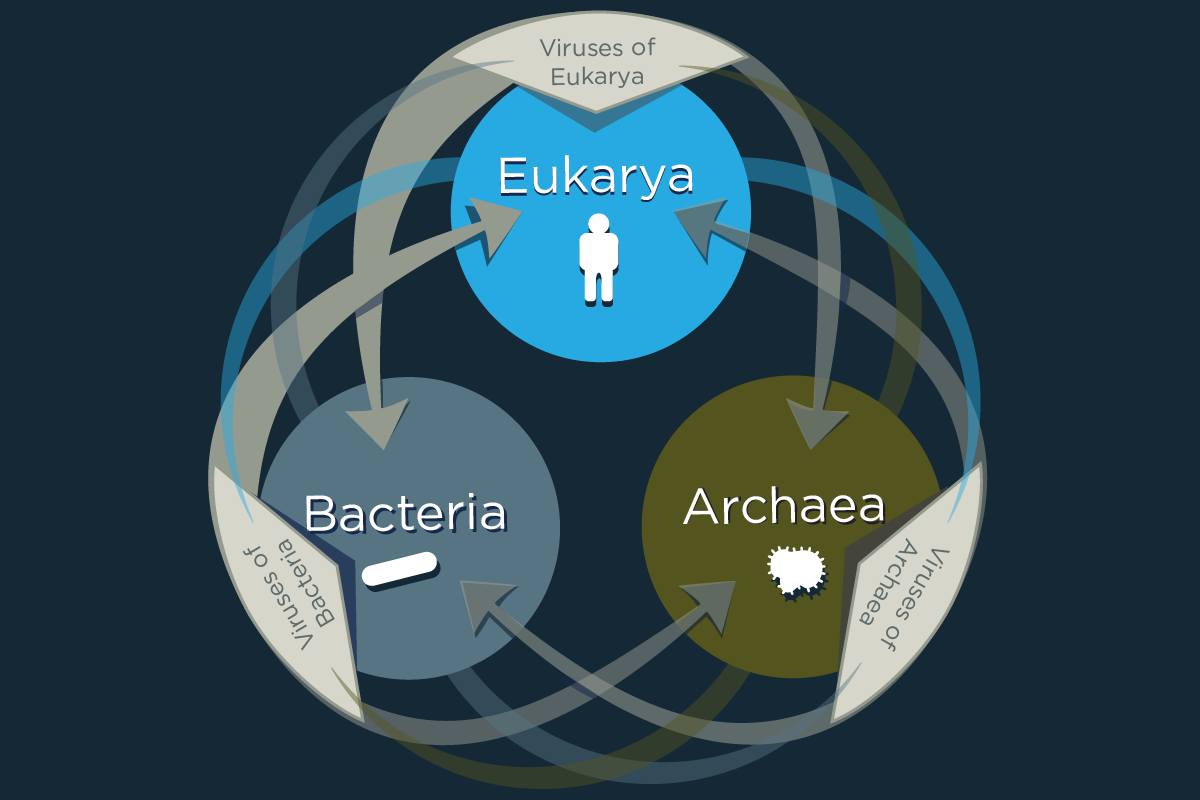
Study:Viruses Share Genes With Organisms Across The Tree Of Life(图)
Viruses Share Genes Organisms Across Tree Of Life
2017/12/19
A new study finds that viruses share some genes exclusively with cells that are not their hosts. The study, reported in the journal Frontiers in Microbiology, adds to the evidence that viruses swap ge...

Separated Since the Dinosaurs,Bamboo-Eating Lemurs,Pandas Share Common Gut Microbes(图)
Bamboo-Eating Lemurs Pandas Share Common Gut Microbes
2017/12/19
Bamboo specialization is one of the most extreme examples of convergent herbivory, yet it is unclear how this specific high-fiber diet might selectively shape the composition of the gut microbiome com...
PARTNERS IN PARASITISM,LICE AND THEIR BACTERIAL SIDEKICKS SHARE LONG HISTORY
PARTNERS IN PARASITISM LICE AND THEIR BACTERIAL SIDEKICKS SHARE LONG HISTORY
2017/4/27
A Florida Museum of Natural History study provides new insights into the complex, shared history between blood-sucking lice and the vitamin-producing bacterial sidekicks that enable them to parasitize...
We device a general secret sharing scheme for evolving access structures (following [KNY16]). Our scheme has (sub)exponentially smaller share complexity (share of ii'th party) for certain access struc...
A Tale of Two Shares: Why Two-Share Threshold Implementation Seems Worthwhile-and Why it is Not
Threshold Implementation Paired t-test Lightweight Cryptography
2016/5/5
In this work, we explore the possibilities for practical Threshold Implementation (TI) with only two shares in order for a smaller design that needs less randomness but is still first-order leakage re...
Coral reefs face many threats. Ocean acidification, algal takeover caused by overfishing and exploding populations of harmful microbes all jeopardize the health of the world’s most productive and dive...
How to Share a Secret, Infinitely
Secret sharing threshold access structure dynamic access structures
2016/2/25
Secret sharing schemes allow a dealer to distribute a secret piece of information among several
parties so that any qualified subset of parties can reconstruct the secret, while every unqualified
su...
Cryptanalysis of ring-LWE based key exchange with key share reuse
lattice techniques LWE ring LWE
2016/2/23
This paper shows how several ring-LWE based key exchange protocols can be
broken, under the assumption that the same key share is used for multiple
exchanges. This indicates that, if these key excha...

Carnegie Mellon,Stanford researchers devise method to safely share password data(图)
Carnegie Mellon Stanford researchers share password data
2016/3/2
An unfortunate reality for cybersecurity researchers is that real-world data for their research too often comes via a security breach. Now computer scientists have devised a way to let organizations s...
Are you The One to Share? Secret Transfer with Access Structure
oblivious transfer access structure secret sharing
2015/12/22
Sharing information to others is common nowadays, but the question is with
whom to share. To address this problem, we propose the notion of secret transfer with
access structure (STAS). STAS is a tw...


